Documentation
The problem I am trying to solve here is: How to securely
transmit secret data over the internet,
without third party/enemy knowing that such secrets are being
transmitted.
Secret messages are of course protected by a password or
multiple passwords and hidden in images.
Password
First problem here is how do I securely send password to my
friend without the enemy knowing?
Telephone? SMS? Skype? WhatsApp? Signal?
All these media are being monitored and most of them are
recorded.
Signal seems to be more secure than others, but I wouldn't say
it can be 100% trusted.
My friend may be in another country and I may not have the
possibility to give him password
simply written on a piece of paper. If I tell him the password
openly using my mobile phone,
then there is a risk that my Android phone will record
conversation with my friend and send it to a third party,
even if Signal is an honest app with no backdoor in it, there
may be other programs (malware)
running in the background and recording all I am saying,
regardless whether Signal is on or off.
Also password should be difficult because all easy passwords
are prone to brute force/dictionary attacks.
So, if I try to spell difficult password, containing special
characters, small and capital letters and numbers
then there is likely to be a mistake, and I will have to
repeat it. All that is very risky and takes time.
What if I have an innocent conversation with my friend, and
only ask him about how he feels,
maybe talk about the weather, a walk in the park I had the
other day, or the news?
Who will know for sure that I am negotiating password with my
friend?
Nobody. This is called plausible deniability.
This is what the first tab called "Password" is for:
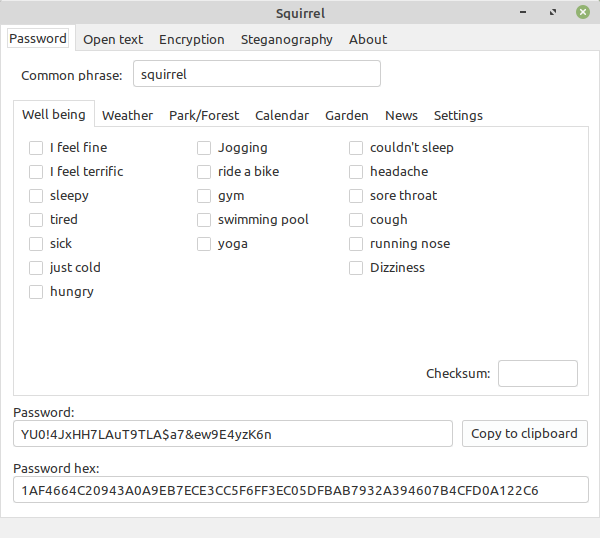
The idea can be easily explained by the following example:
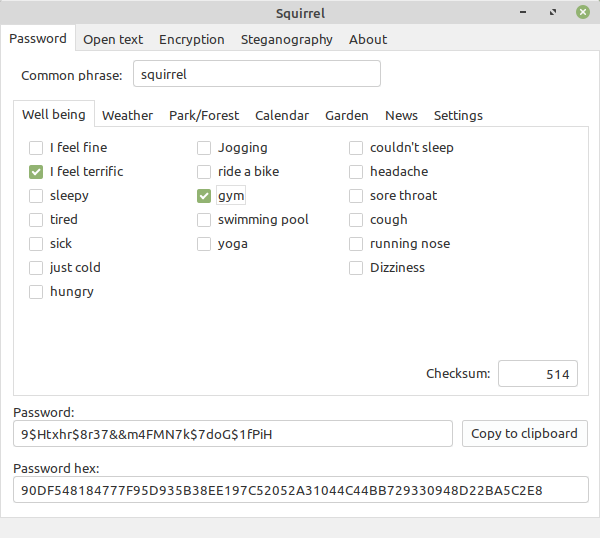
I begin with asking my friend: How are you?
and he responds: I feel terrific, I went to the gym today.
We both select "I feel terrific" and "gym".
As you can see, the password is automatically re-calculated
each time user clicks a checkbox:
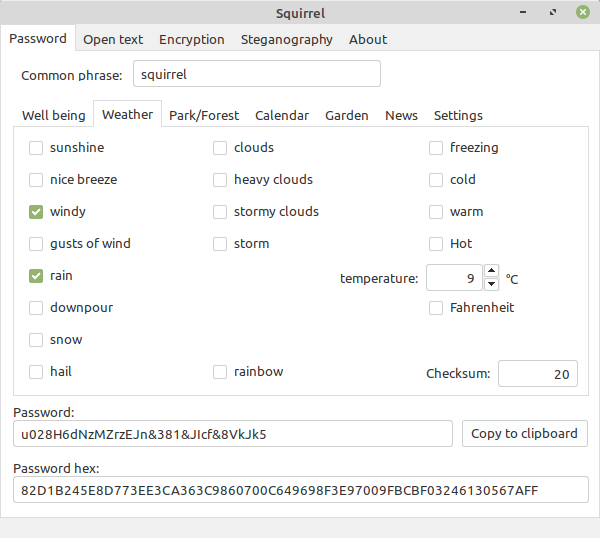
The conversation then proceeds to another topic, weather for
instance:
I can make a remark that: It is windy and raining, but it is
not very cold, it is 9 degrees C.
We both click "windy" and "rain", then select 9 as the
temperature.
If I didn't mention the temperature, it should stay as it is
(21), even if it is freezing cold.
There is also Fahrenheit scale for those people who use it.
There can be schemes within schemes. We can agree with my
friend
that what he says about the weather counts, and what I say
about the weather doesn't.
There may be additional key-words not included in this
program,
which combined with words in the Squirrel are real trigger for
the checkbox to be clicked.
Even yawning may mean something. Non verbal communication is
priceless
as long as both sides precisely agree to what each gesture
means.
Checksums show the state of checkboxes on each page.
They are there to practice.
The should not be read over the phone, when negotiating
password, as it may arise suspicion.
Common phrase in the first picture is the word me and my
friend agreed upon.
It doesn't have to be complex, but it should be unique in a
sense that only me an my friend know about it.
Could be the name of a childhood pet, make or model of the
car, whatever.
Preferably that is something we have agreed face to face.
Yes it is preferable to meet face to face at least once,
exchange some secrets and then keep these secrets offline
on a "Red" computer, never expose them (by typing them on a
keyboard for instance) on a "Black" computer,
that is computer connected to a network.
This way we can generate new and very secure password by means
of an innocent conversation,
and it is easy. It takes only the amount of time as the Signal
conversation itself.
It is good to have computer mouse which doesn't make a sound
when clicking a checkbox,
so the sound of the mouse doesn't get recorded over the phone
during conversation,
or we can use touchscreen instead. Most modern laptops have
touchscreens.
Password is calculated based on the state of the passphrase,
checkboxes, temperature, and calendar (but only if "use
calendar" is selected).
There are over 100 checkboxes which give more than 2 to the
power of 100 of combinations,
which combined with passphrase and calendar helps to create a
very very unique and impossible
to guess password. Please experiment with password creation
for a while.
Changing even one checkbox gives a completely different
password.
But that is not all.
Each checkbox does not simply represent a single zero or one
as some of us might think at this point.
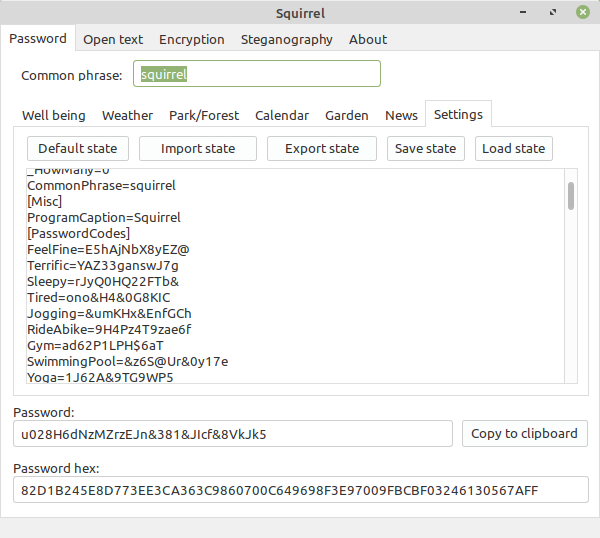
On the password settings page (as on the screenshot above)
we can see password codes associated with each checkbox.
For instance checkbox: "I feel fine" has default password
code: E5hAjNbX8yEZ@
associated with it. When "I feel fine" selected, then code
E5hAjNbX8yEZ@
is applied to our password, making it more unique.
Password is a result of a hash value generated from
combination of relevant password codes,
passphrase, temperature value and calendar (only if selected).
As it is easy to guess at this point it is enough to click
just a few checkboxes
to get a password that is impossible to guess.
And now the best part.
All these password codes are default.
It is strongly recommended to take some time and change all of
them,
if we want to have truly unique password generator.
It is enough to change just one letter in each of these
password codes.
Please remember that password codes together with passphrase
form set of secrets that should be agreed upon before secret
communication takes place.
After password codes have been changed we need to press
"Export state" button,
so the next time Squirrel is loaded into memory it will have
our secrets, rather than default secrets.
So ideally me and my friend prepare a file with secrets, press
"save state" button to save
the secrets into a text file, I then share file with my friend
using USB stick, and we are ready.
We have to have the same set of secrets to be able to
communicate with each other.
What is interesting is that "Save state" button option also
saves state of all the checkboxes,
so even if they are not mentioned in an innocent conversation
later on,
they will be checked by the default, and the enemy will never
know that,
unless they physically get hold of the "Red" computer.
By sharing different set of secrets with different people we
can create different circles of trust.
For instance let's say I have three friends: Mike, Bob and
Jerry.
I create three files named respectively: Mike.txt, Bob.txt,
Jerry.txt, give each friend respective file.
I can then start communicating with each of my friends
separately and securely using Squirrel,
but Bob will never know what I told Mike even if I posted an
image containing message to Mike
on an Instagram. It works both ways. If Bob prepares his set
of secrets and shares it with Jerry,
then I will never know what he sent to Jerry in an image.
Moreover I won't know that he in fact embedded any message in
the image at all.
The image could be just an image, and it so happens that he
posted it on an Instagram.
If for instance Jerry betrays me and starts collaborating with
an enemy against me,
he won't be able to crack any of my passwords that I generate
to communicate with Mike or Bob,
even if Jerry was capable of intercepting my phone calls to
Mike and Bob.
He won't be able to tell for sure that I am using Squirrel
when communicating with Mike or Bob,
all he will hear is an innocent conversation about weather and
news.
I may have many friends and may talk with all of them about
weather,
and there is nothing suspicious about that, that is what
people do all the time.
If an enemy breaks into my home and tries to physically get
hold of my "Red" computer,
they may find that it is impossible for them to find it.
It may not even be a computer but a small USB stick which
looks like this:

The length of this USB stick is smaller than a diameter of one
euro coin,
so it is very easy to hide. This USB stick is more than
capable of holding
entire Linux distribution such as Puppy Linux, Tiny Core Linux
or Tails Linux,
to name a few. "Red" computer becomes "Red" when it boots from
such
USB stick containing secret codes. At other times that
computer is just
normal computer running different OS from an ordinary hard
drive.
However such computer should NEVER be connected to a network,
even if it is not running as "Red", as a precaution.

